Stay Pragmatic
Risk management should not become an end in itself. It is primarily a tool to prevent potential problems and avoid disruptions to your company's operations. The goal is to identify the most significant issues you may face and address them effectively.
- What could most endanger or even paralyze your business?
- What could halt your operations, cause financial losses, or result in fines?
There are many ways to identify risks. The method you choose always depends on the type of risks you face, your experience and your overall baseline.
It should also be emphasized that there is no single right way and in practice a combination of different methods and techniques is used. There is no single right way. All that matters is identifying the right list of real, fundamental risks in your circumstances.
Name the Risks Correctly, with clear Risk Statement
- Correct and clear name will help reduce misunderstandings
- Do not confuse the name of the risk, its causes and consequences
- See the basic rules for naming risks and Risk Statement
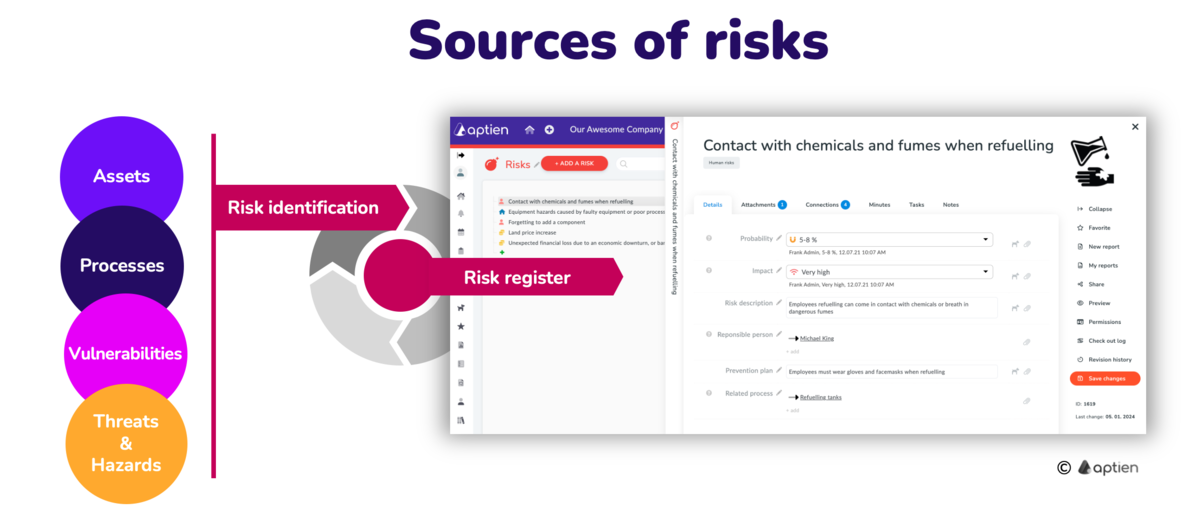
Start with the Sources of Risks
It is important to always correctly identify the sources of danger and your risks. The following ways will help you to find them. Risk always arises from something, somewhere. It never hangs in a vacuum. Most of the risk comes from some process or some asset you have in your company.
The Analysis is Followed by Evaluation and Prioritization
Once you have identified the risks, you need to assess and prioritize them.