Threat-Based Risk Analysis
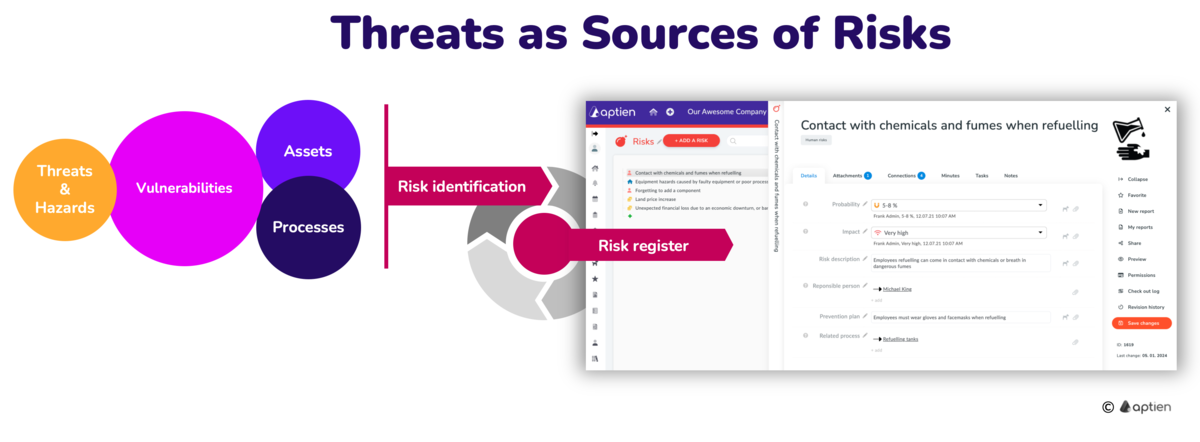
Threat-based risk analysis extends the scope of risk identification beyond an organization's assets and processes. This method primarily uses lists of known and existing threats, typically those that can be compared to the normal state over a period of time.
Procedure for Threat-Based Risk Analysis:
- Create a list of known threats.
- Assess which of your assets and processes are at risk from these threats.
- Make a list of the risks that these threats can cause.
- Based on existing and known threats, identify possible new risks that may arise.
Considerations When Analyzing Threats:
- Threats can increase the likelihood of known risks.
- Supplementing risk assessment with threat analysis creates a more effective risk management strategy.
- This approach should complement other methods of risk identification, as it captures a broader range of potential risks.