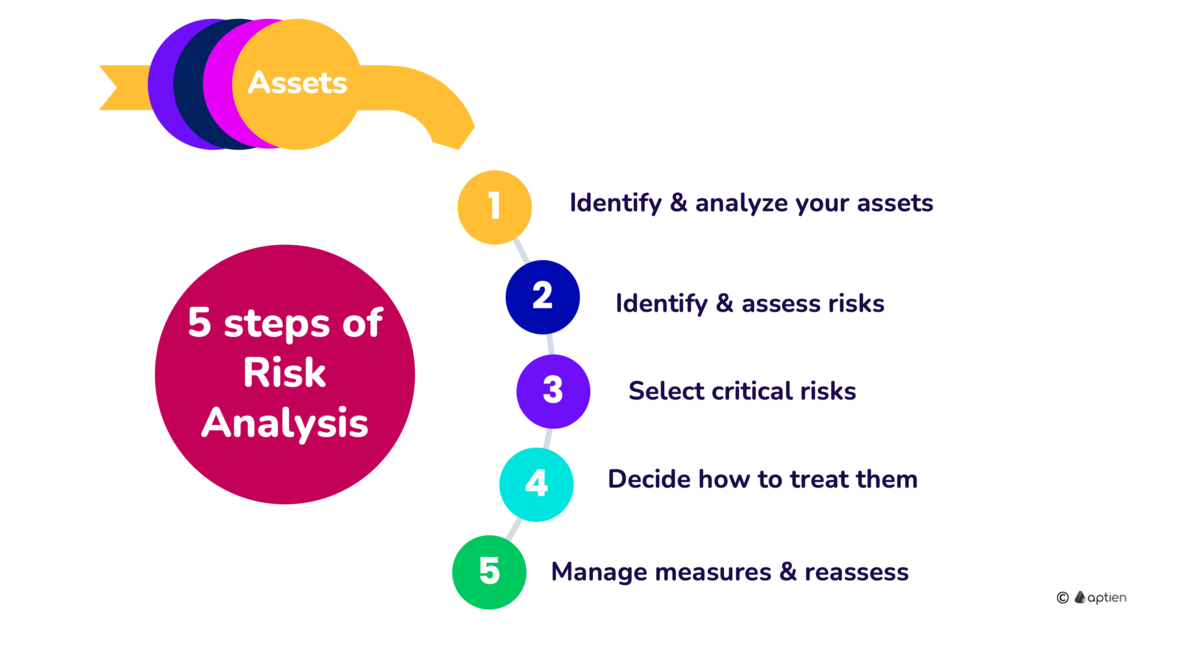
5 basic steps of Asset-based Risk Assessment
Asset-based Risk Assessment is one way of identifying risks. We guide you through the process, which is based on asset valuation and consists of five basic steps.
Creating a risk catalog in a company is certainly a challenge. It is therefore important to know where to start and how to proceed with the creation. In this article, we will look at one of the most common ways of creating a risk catalog, based on a company asset register. This method is quite widely used and is especially common in the information security field.
We have put together 5 basic steps to guide you through the risk assessment so that you don't drown in it. There are certainly other approaches, this is just one possible approach.
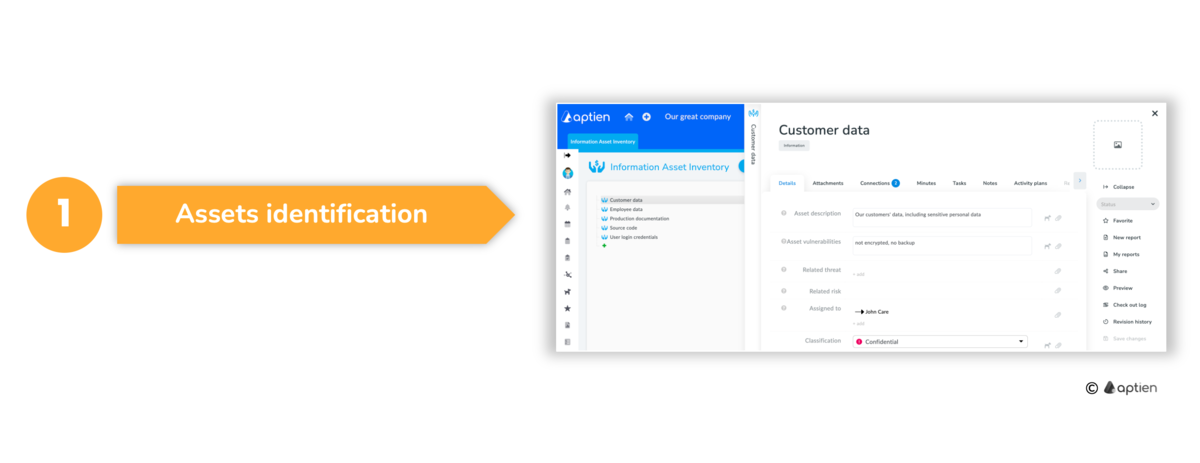
Step 1: Identify and name your business assets
Assets, along with processes, are sources of risks. As a starting point, you need to create an inventory of company assets. This inventory will serve as the foundation for your risk analysis and assessment. Identify assets that hold significant value for the company or that, if compromised, could pose a risk. By doing so, you’ll gain clarity on priorities and be able to focus on the essential corporate assets – those that truly matter to the company. Use an asset register to set up basic asset types such as:
- Physical Assets: Buildings, equipment, machinery, and infrastructure.
- Human Assets: Employees, contractors, and their skills, expertise, and health.
- Information Assets: Data, intellectual property, trade secrets, and proprietary processes.
- Reputational Assets: Brand equity, customer trust, and public perception.
- Financial Assets: Cash, investments, and accounts receivable.
- Technological Assets: IT systems, software, and networks.
- Services: e.g. electricity supply, cloud services
For each asset type, enter and name your business assets. Be specific.
Identify and assign asset owners
- Each named asset should have a business owner within the company who is responsible for it. It should be someone in the top management of the company who has responsibility, but also authority over the asset. Assets are sources of potential threats and vulnerabilities.
Step 2: Identify risks
- Identify risks for each asset
- Collaborate with asset owners, as they are most familiar with the risks associated with their assets.
- Owners bear the responsibility for mitigating risks and possess sufficient authority to manage them.
- Utilize the risk register to describe individual risks.
- Recognize that every asset is susceptible to certain threats and has its unique vulnerabilities.
- Thoroughly analyze each asset to identify and map potential threats and vulnerabilities.
- Keep step three in mind and concentrate on your critical assets.
Step 3: Assess risks
Prioritize the List of Risks:
- It’s essential to prioritize the risks identified in the previous step.
- Priorities are crucial because they help you focus on the most critical risks.
- Remember that you can’t address all risks simultaneously.
Use a Risk Matrix:
- A risk matrix is a valuable tool for visualizing risks based on their probability and impact.
- Evaluate each risk from the previous step by considering both its impact and probability of occurrence.
Impact and Probability:
- The impact of a risk is influenced by the value of the asset.
- The probability of risk occurrence is tied to the asset’s vulnerability and existing threats.
High-Priority Risks:
- Risks with a high degree of probability and impact deserve the highest priority.
- Addressing these risks promptly is crucial, as they pose the most significant danger.
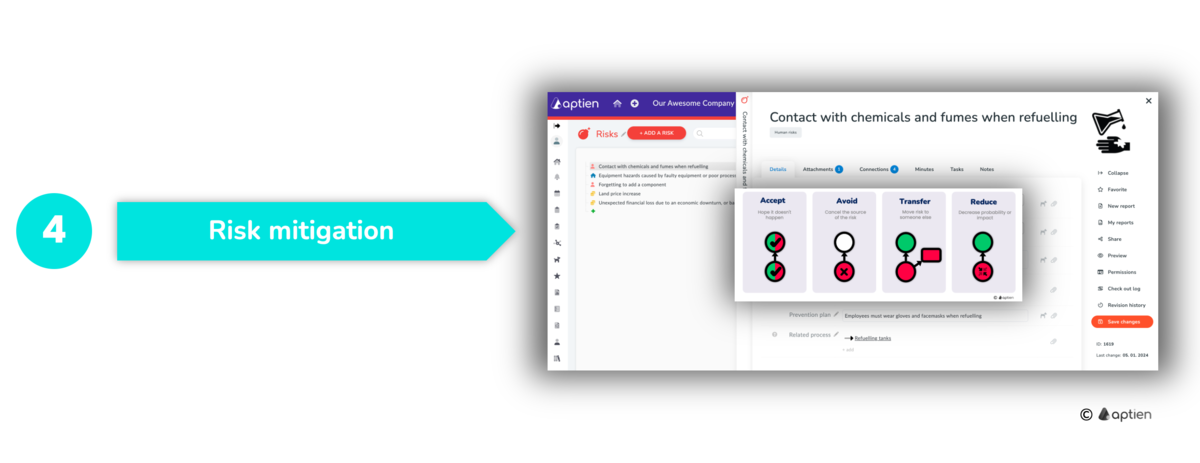
Step 4: Decide How to Handle Risks
Based on priorities, proceed to the final step, which involves determining how you will address each risk. From the previous step, select the most critical risks and decide how to handle them—how to treat each individual risk. Remember that risks can never be completely eliminated; you can only reduce their likelihood or impact.
Choose a Strategy for Each Risk:
- Evaluate the best approach for managing each risk.
Implement Measures and Preventive Actions:
- Develop specific measures and preventive actions for the selected risks.
Assign Owners to Each Measure:
- Assign responsibility for implementing these measures.
- Use tasks to manage their execution over time.
Document Meetings and Outcomes:
- Keep records of meetings and share them through notes.
Focus on the Top 10 Critical Risks:
- Concentrate your efforts on addressing the most crucial risks.
Regular Status Evaluation Meetings:
- Consider holding regular meetings to assess the risk status.
Step 5: Conduct Regular Reviews
The situation is constantly changing, and you must adapt to these changes. Some risks may disappear, their probabilities may shift, and new risks may emerge. It is essential to keep your activities up-to-date in this regard. This way, you won’t waste time addressing risks that have already vanished, and you’ll be aware of any newly arising risks.
- New risks appear, while old ones may fade away or decrease in significance.
- Regularly reassessing the situation is crucial,
- Annual cycle is the most suitable timeframe for doing so.