Meaning of a Threat
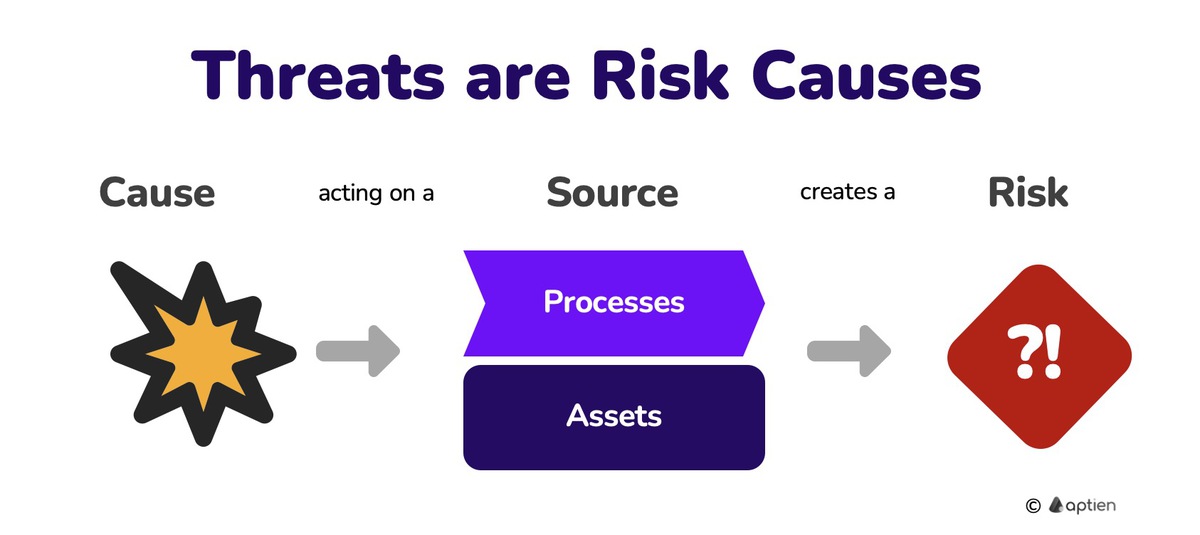
Threat is an event, situation, or action that can create risk and cause loss, damage, or unavailability of an asset, process, or plan. Organizations need to protect their assets and processes against threats—especially in the areas of information security, physical security, and business continuity.
- Threats are triggers for risk scenarios or incidents.
- They affect business assets or processes and can cause a risk event.
- They are conditions or mechanisms that turn potential risks into actual incidents.
- Threats can be intentional (attack, sabotage), unintentional (human error), or accidental/natural (natural disaster).
Why should small businesses care about threats?
Small and midsize businesses are frequent targets of cyber threats (e.g., phishing, ransomware) because they typically do not have the same level of protection as large enterprises. They can also be affected by operational threats (e.g., supplier outages) or workplace safety risks. Even a single incident can have serious financial consequences for a smaller company.
Examples of common threats small businesses most often face
- Cyber threats: phishing, ransomware, malware, DDoS attacks, social engineering.
- Operational threats: supplier/vendor failures, dependence on key personnel.
- Safety risks (workplace hazards): workplace injuries, OSHA violations.
- External threats: theft, vandalism, natural disasters, changes in market conditions.
- Compliance and regulation: failure to meet legal or industry requirements (e.g., HIPAA, GDPR, ISO, OSHA).
How can small businesses prepare for these threats?
- regularly conduct risk assessments,
- identify and document key threats and hazards,
- train employees in cybersecurity and workplace safety,
- have a business continuity plan in place,
- use simple risk management tools to record and track threats.
Threat vs. Hazard
Sometimes “threat” and “hazard” are used interchangeably as sources of risk. In simple terms, they are “things that can harm assets, processes, or people.” Risk management professionals use a clearer distinction:
- In cybersecurity, business continuity, and strategic management, the term “Threat” is commonly used.
- In workplace safety (OHS, OSHA), the term “Hazard” is more common (e.g., chemical hazards, fire hazards).
Threat
- A threat is the potential for a specific harmful event to occur, such as a concrete incident or attack.
- For example, a DDoS attack targeting a known vulnerability in a process or asset is a threat.
- Examples include cyberattacks, external actors, and intentional or unintentional events.
Hazard
- A hazard is a condition or source with a more permanent nature that can lead to a threat or risk (for example, a machine that can cause injury).
- Common workplace hazards include chemical, physical, and ergonomic hazards.
Threats can cause various adverse outcomes
- Threats have the potential to result in injury, property damage, business disruption, or environmental harm.
- Organizations typically lack control over whether a threat or danger occurs or materializes.
- These events often arise from external factors beyond an organization’s direct influence.
- Early threat identification allows organizations to be prepared.
- By anticipating threats, they can mitigate their impact through preventive measures.
- Identifying threats is a crucial step in risk analysis.
- It helps pinpoint vulnerabilities and assess potential consequences.
- By identifying the threat in advance, the organization can prepare for the threat and mitigate its impact
- A threat is something that your assets should be protected against
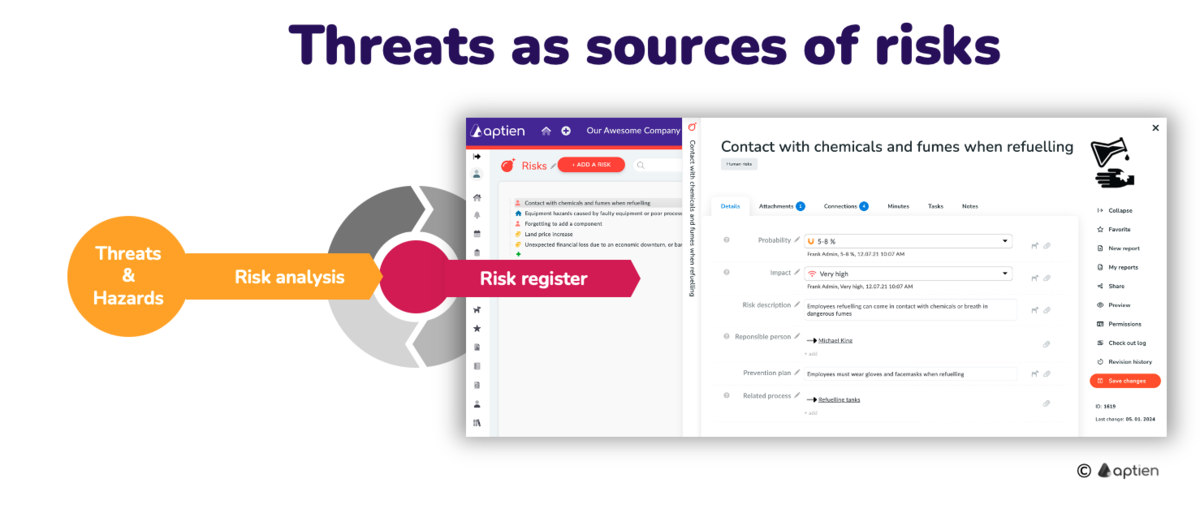
How to Maintain Threat Register in Aptien
Maintaining a threat register is essential for effective risk management. Automate the tracking and updating of threats. Here are some steps to keep a comprehensive and up-to-date threat catalog:
- List of Potential Threats : Identify and list all potential threats that could impact your organization. This includes both external threats (e.g., natural disasters, cyber-attacks) and internal threats (e.g., human error, system failures).
- Categorize Threats: Organize threats into categories such as physical, cyber, operational, and environmental. This helps in understanding the nature and source of each threat.
- Detail Each Threat: For each threat, provide a detailed description
- Link to Assets and Processes: Connect each threat to the specific assets or processes it could affect. This helps in assessing the overall risk and prioritizing mitigation efforts.
- Link to Risks: Link each threat to the specific risk which can trigger.
- Regular Updates: Continuously update the catalog to reflect new threats and changes in the organization’s environment.
Detail Each Threat: For each threat, provide a detailed description
- Threat ID: A unique identifier for tracking.
- Description: A brief overview of the threat.
- Impact: Potential consequences on assets or processes.
- Likelihood: The probability of occurrence.
- Mitigation Measures: Steps to reduce or manage the threat.