Overview of All Known Threats
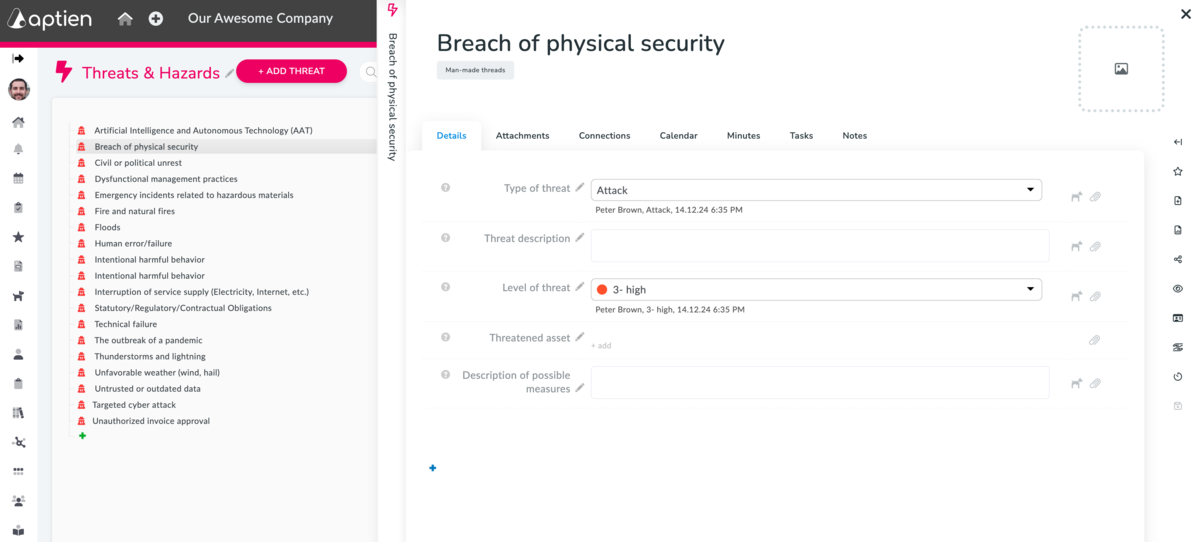
A threat register is designed to compile a comprehensive list of threats that could impact your assets or processes. Use the threat register alongside the risk organizer, which provides an overview of risks, and the action plan, where you document corrective or preventive actions for each risk (see measures organizer).
Maintaining a threat register is essential for effective risk management.
Automate the tracking and updating of threats.
- List of Potential Threats : Identify and list all potential threats that could impact your organization. This includes both external threats (e.g., natural disasters, cyber-attacks) and internal threats (e.g., human error, system failures).
- Categorize Threats: Organize threats into categories such as physical, cyber, operational, and environmental. This helps in understanding the nature and source of each threat.
- Detail Each Threat: For each threat, provide a detailed description
- Link to Assets and Processes: Connect each threat to the specific assets or processes it could affect. This helps in assessing the overall risk and prioritizing mitigation efforts.
- Link to Risks: Link each threat to the specific risk which can trigger.
- Regular Updates: Continuously update the catalog to reflect new threats and changes in the organization’s environment.
Benefits of Threat Register
- Comprehensive overview of threats
- Company-wide threat catalog
- Detailed threat profiles with descriptions and follow-up actions
- Analysis of threat impacts