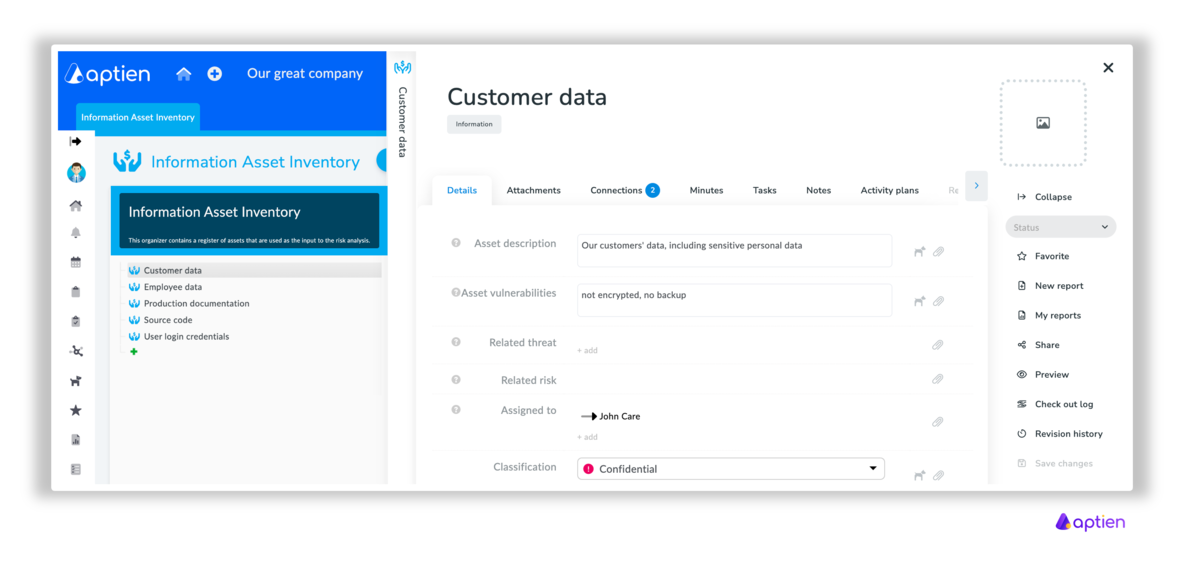
Asset Library: An overview of all primary assets in your organization
For information, cyber security and other cybersecurity regulatory requirements (NIS2, HIPPAA, tec.) , you need to maintain a catalogue of the information assets in your organisation. To do this, the primary assets organizer is used, which is intended to create and maintain an overview, a catalog of all primary information assets in your organization. We recommend using this organizer together with the records of supporting and technical assets, together with risks catalog, vulnerabilities and threats. This will give you a comprehensive overview of all the context you need to manage risk and meet your obligations under NIS2 and the Cybersecurity Act respectively.
- You get an overview of all primary assets
- Comprehensive inventory of primary assets across the company
- Detailed asset card for each individual primary asset
- You manage all dependencies and relations on secondary (support and technical) assets, risks, vulnerabilities and threats
Creating information asset inventory step-by-step
When we help teams with information security, we often start with a workshop with the information security team and management representatives responsible for individual information assets. With the team, we create a list of information assets in the following way:
1. Start with primary assets (data)
- First, focus on your primary information assets, i.e. your data
- Identify the key information that your organization cannot function without. Help yourself with the phrase "if we lose them, we're done" or "if someone abuses them, we have a big problem"
- List 3-10 core information assets, this will help you not drown in detail
- Name the impact of the destruction or loss for each primary asset. Help yourself imagine what the consequence of their loss will be for you on a scale from within "we don't know" until "it will ruin us"
- Assess whether it is really a primary asset and not a supporting one
- Repeat points 2-5 until you have a satisfactory result, being careful not to include supporting assets.
2. Create a list of supporting assets to the primary assets
- Identify the key systems, software, hardware or infrastructure where your data (primary assets) is stored
- Proceed from each primary asset with the question "where and how is the data stored"
- Name the impact for each one. How will their unavailability affect you? On a scale from "nothing happens" to "nothing will work"
- Repeat points 1-3 until you have a list of everything that must work for your company to work
Dependencies Between primary and supporting assets
- For managing risks you must also record dependencies between primary and supporting assets
- One primary asset may be dependent on several supporting assets
- A single supporting asset may support multiple primary assets
- In Aptien, you maintain this information as links between your organizers of primary and supporting asset inventories