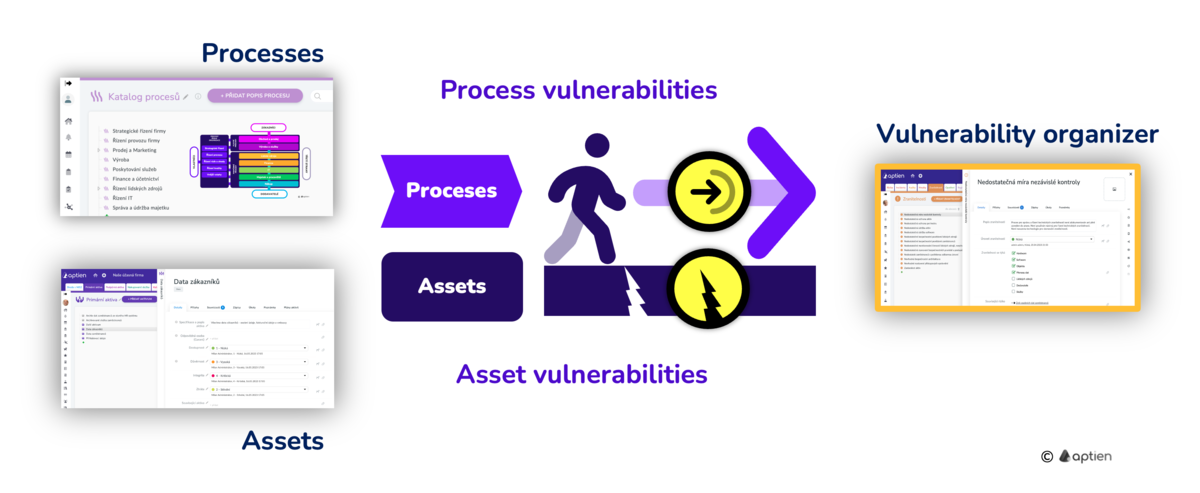
Overview of vulnerabilities of your processes and assets
For risk management and physical, information or cyber security purposes, a list of vulnerabilities arising from assets, processes or information system should be maintained. Keep the list of discovered vulnerabilities here and follow their sources - processes or assets.
- You get an overview of all vulnerabilities
- You keep connections between vulnerabilities with individual assets or processes
- You can also link vulnerabilities to individual risks
Vulnerability catalog as part of the risk management system
- Identifying and maintaining an overview of vulnerabilities, either in the form of a separate catalog or for individual assets or processes, is an integral part of risk analysis and management
- You manage vulnerabilities in the vulnerability catalog and link to their sources
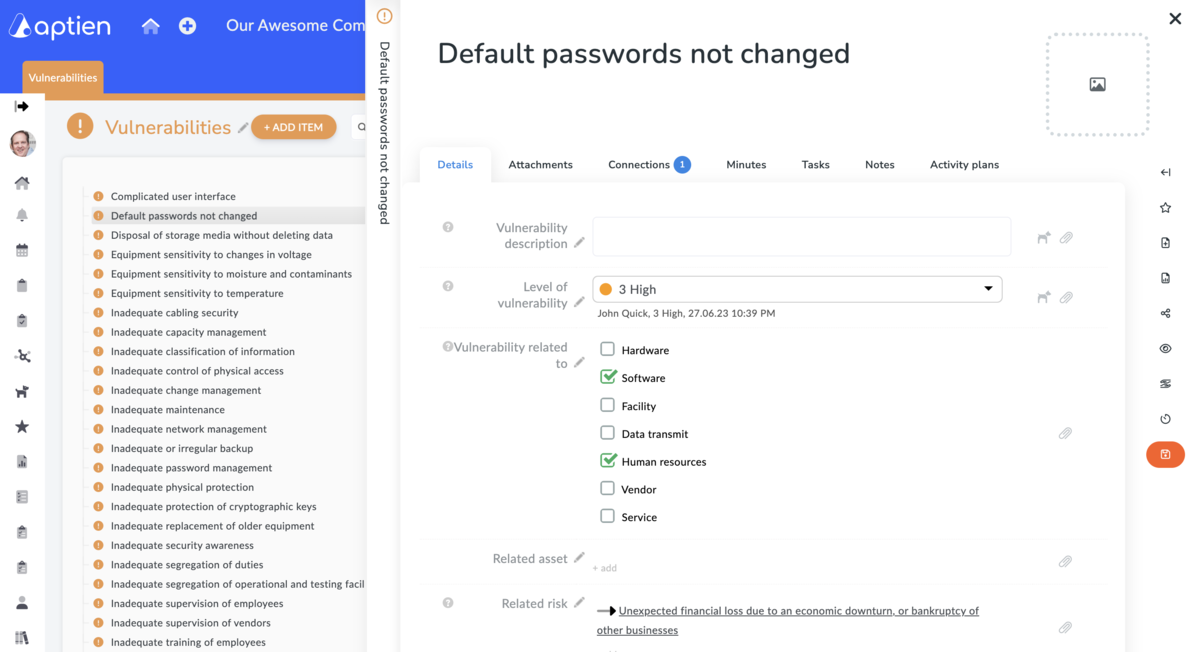
Information in the organizer of vulnerabilities for cybersecurity
- Vulnerability ID
- Vulnerability description
- what the vulnerability affects (software, hardware, etc.)
- related asset
- associated risk
For information security, cyber security or NIS2 requirements, a list of of your information system must be maintained. The vulnerability organizer, is designed to catalog and manage all vulnerabilities It is recommended that this organizer be used in conjunction with a catalog of threats, and with primary assets records.