Overview of all Cyber and Information Threats in Your Organization
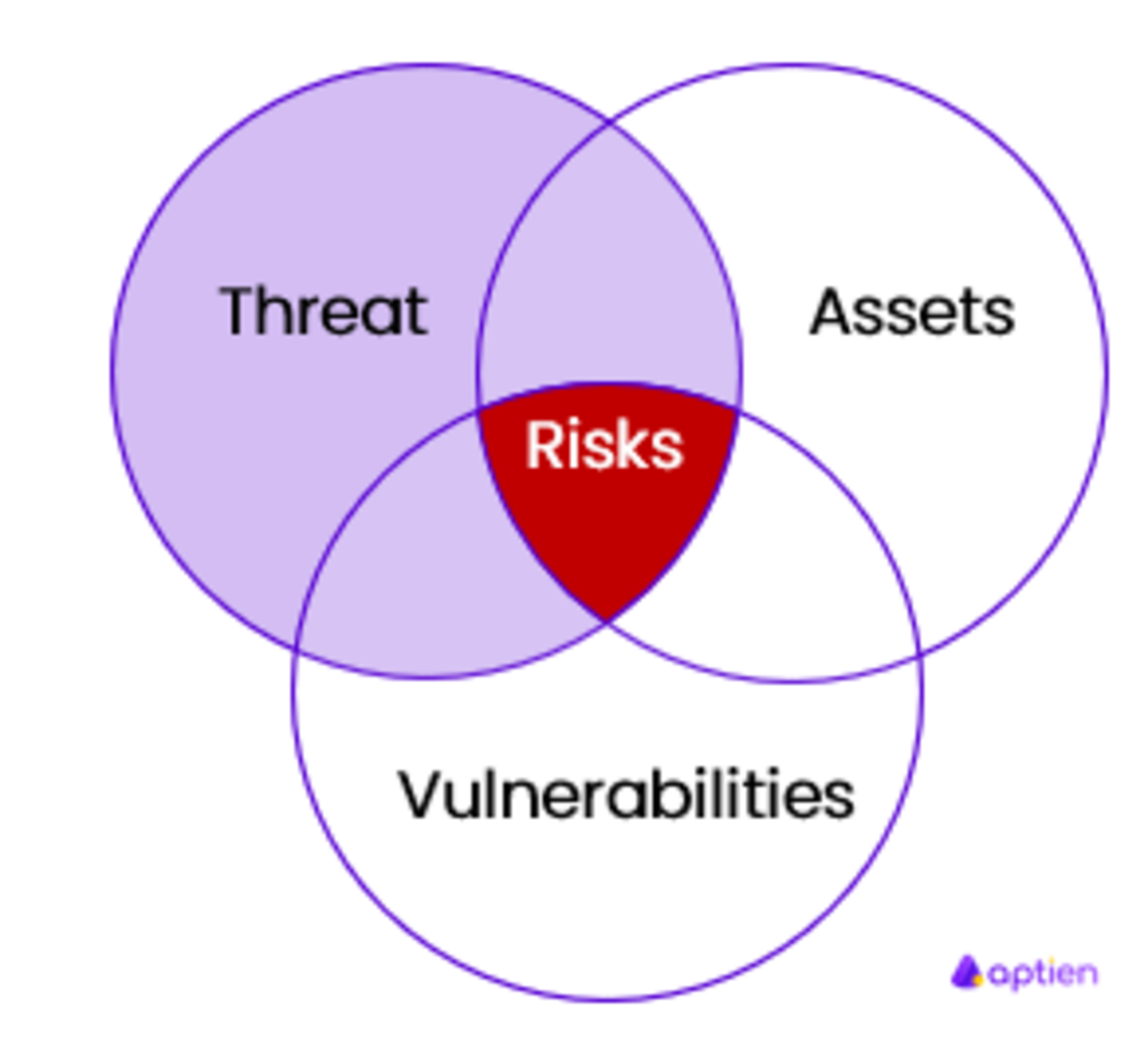
For the purposes of information and cybersecurity and NIS2 requirements, it is necessary to maintain a catalog of information threats in your organization. This is facilitated by threat tracking, which is intended for the creation and management of the catalog of all information threats in the organization. We recommend using this tracking together with records of primary, supportive, and technical assets, as well as risk assessment records and vulnerabilities. This will provide you with a comprehensive overview of all the relevant connections you need for risk management and to fulfill obligations under NIS2 and the Cybersecurity Act.
- You will gain an overview of all information threats.
- An information threat catalog across the entire organization.
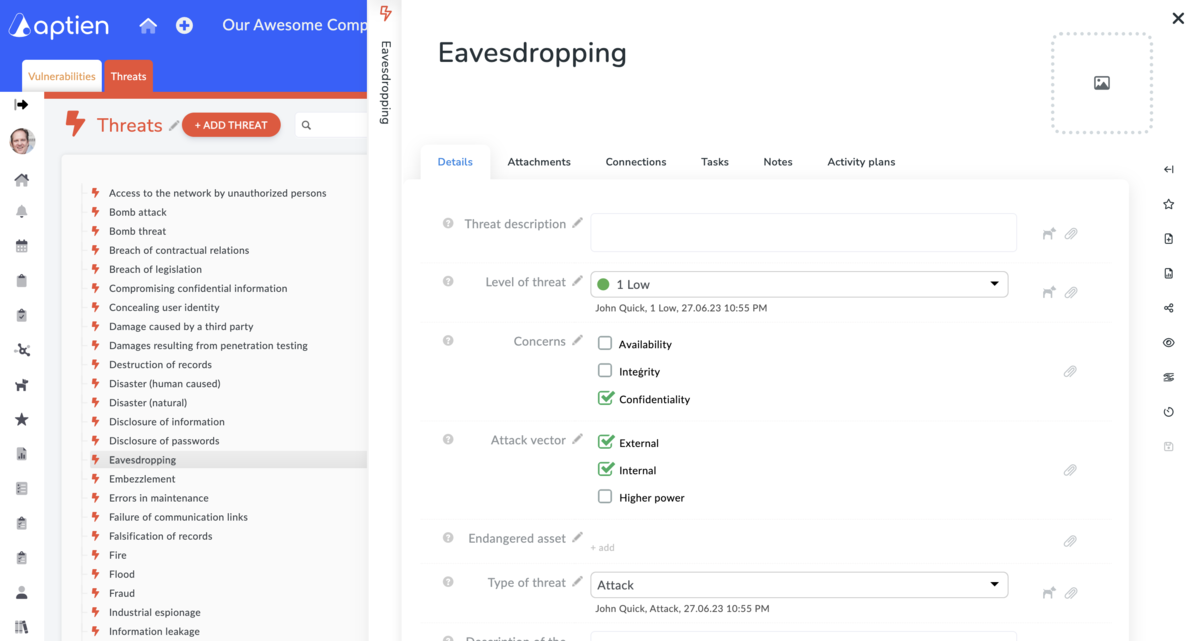
- Detailed threat card for each individual threat.
- Linkage to primary, supportive, and technical assets.
- Association with risks.
Information in the Threat Catalog
- Threat ID
- Threat description
- Whether the threat pertains to availability
- Whether the threat pertains to integrity
- Whether the threat pertains to confidentiality
- Description of the level of threat
- Linkage of the threat to risks
Katalog hrozeb jako součást systému řízení rizik
Identifikace a vedení přehledu hrozeb je nedílnou součástí analýzy rizik pro potřeby informační bezpečnosti, NIS2 a zákona o kybernetické bezpečnosti.