Vulnerability-Based Risk Assessment
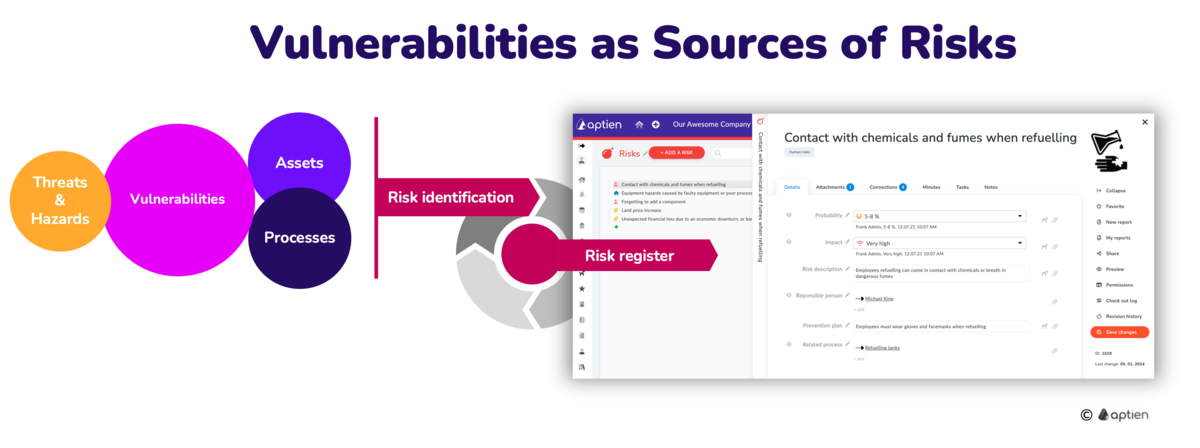
Vulnerability-Based Risk Assessment expands the scope of risk identification beyond an organization’s assets and processes. It involves leveraging lists of known vulnerabilities, weaknesses and deficiencies, which can be sourced from the market, experts, manufacturers, or other entities. These vulnerabilities may exist in technology, such as various software, operating systems, or hardware, making them susceptible to exploitation by attackers. Additionally, there may be procedural weaknesses, such as emerging fraud techniques or novel social engineering methods, which can also pose risks.
- By analyzing these known vulnerabilities, organizations can identify new potential risks and assess the consequences that may arise from their exploitation.
- Vulnerabilities can also increase the likelihood of known risks
- Integrating vulnerability-based risk assessment enhances the risk identification.
- However, it’s important to note that this approach should complement existing risk identification methods rather than replace them. Traditional risk forecasts may not always capture the full spectrum of risks an organization.
Possible List of Known Vulnerabilities for Risk Management
1. General Risk Management Vulnerabilities
- COSO Framework: Addresses enterprise risk management and highlights vulnerabilities related to internal controls, governance, and operational risk.
- ISO 31000: Focuses on risk management processes, identifying systemic vulnerabilities like poor communication or inadequate monitoring.
- NIST Risk Management Framework (RMF): Includes specific security vulnerabilities and control deficiencies for managing risks in IT systems.
- BCP and DR Frameworks (e.g., ISO 22301):
2. Vulnerabilities in Information Security
- Common Vulnerabilities and Exposures (CVE), A publicly available list maintained by MITRE Corporation.
- Common Vulnerability Scoring System (CVSS).
- National Vulnerability Database (NVD), Maintained by NIST (National Institute of Standards and Technology).
- OWASP (Web Application Security)
3. Industry-Specific Vulnerability Lists
- HIPAA Security Rule Checklist (for healthcare)
- PCI DSS (for payment systems):
- Sectors like energy or transportation have specific lists from organizations like CISA.
4. Lists of Physical and Environmental Vulnerabilities
- Various lists focus on vulnerabilities to physical assets
- Inadequate environmental protections (e.g., fire or flood risks).
How to perform a risk analysis based on vulnerabilities
1. Monitor Known Vulnerabilities Regularly:
- Keep a close eye on the list of known vulnerabilities.
- Regular monitoring ensures that you stay informed about any potential risks.
2. Focus on Technology Vulnerabilities of Technologies You Use
- Concentrate on vulnerabilities specific to the technologies you use.
- Understanding these weaknesses is crucial for effective risk analysis.
3. Update Existing Risks for New Vulnerabilities
- When a new vulnerability emerges, update the associated risks rather than creating entirely new risk assessments.
- This approach maintains consistency and streamlines risk management.
4. Implement Necessary Measures After Risk Assessment
- Once you’ve assessed the risk, take appropriate measures to mitigate it.
- Whether it’s patching software, enhancing security protocols, or implementing other safeguards, timely action is essential.
How Aptien helps with vulnerability-based risk analysis
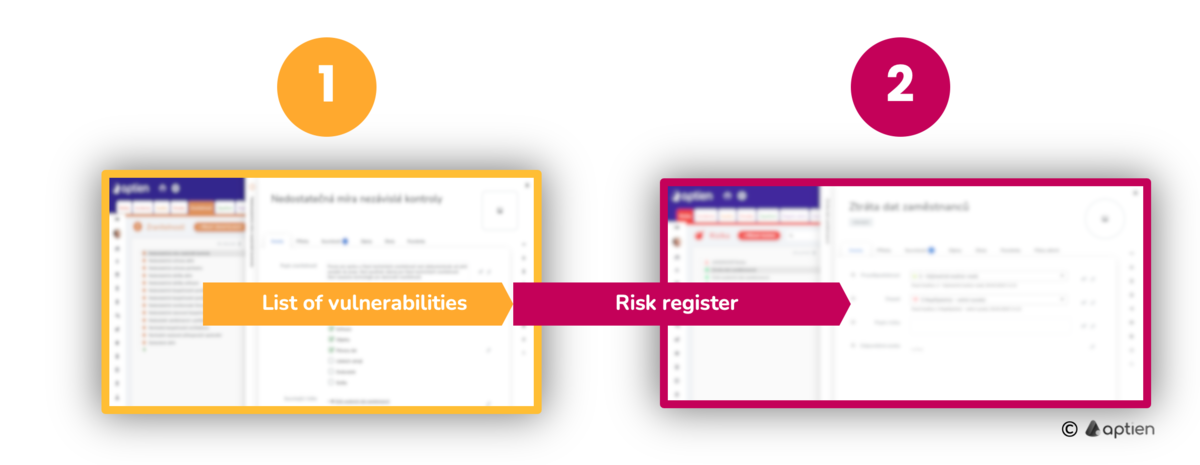
- Start from the vulnerability catalog, where you’ll add a new vulnerability.
- Perform an impact analysis of the vulnerability on existing risks.
- Aptien will assist you in maintaining the connections between vulnerabilities and risks