What is Vulnerability and why it Matters for Businesses
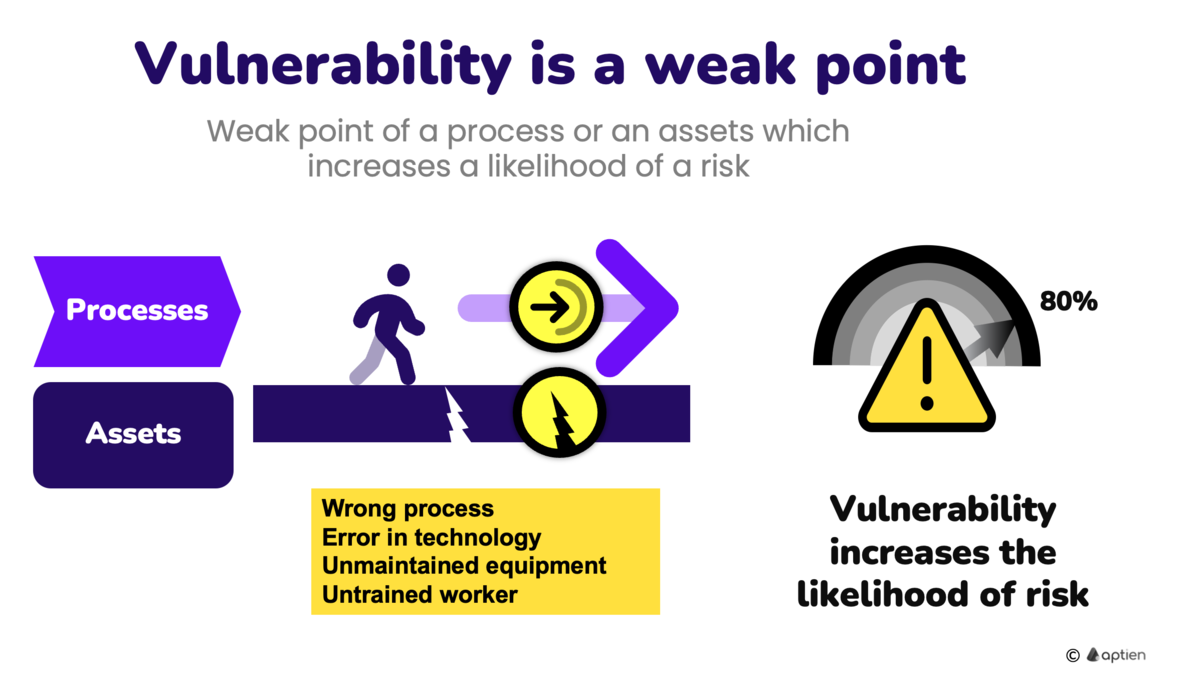
Vulnerability is a weak point, flaw, error, or gap in technology, security environments, processes, people's knowledge, or security measures. In general, it is a weakness of an asset or a business process that exposes them to a higher risk of failure or enables an attacker's unauthorized access or attack.
Examples of Vulnerabilities
- Process Vulnerability: Unrevoked access rights to an application.
- IT Security Vulnerability: Missing or weak encryption.
- Physical Security Vulnerability: An unlockable entry to a room.
- Personal Vulnerability: Poor head protection in the workplace.
Why is it Important to Know Your Vulnerabilities?
Understanding vulnerabilities is crucial because they:
- Increase the likelihood of risk.
- Expose assets to a higher risk of failure.
- Can be exploited by attackers to facilitate unauthorized access or attacks.
Why is it important to know your vulnerabilities
- Vulnerabilities are weak points that you should focus on to eliminate or minimize
- There are many occupational safety and health vulnerabilities or cybersecurity vulnerabilities
- vulnerability-based risk assessment is one of methods how to identify risks
- Along with threats, vulnerabilities help determine risks and are important in their identification and analysis.
How to Name a Vulnerability
Vulnerabilities are some kind of flaws or mistakes, so when naming them, use words like are
- missing, non-existent...
- error in ...
- wrong ...
- insufficient ...
- incorrectly installed...
Most Common Vulnerabilities
- error or defect in technology
- a bug in the software enabling a cyber attack
- insufficiently trained worker
- insufficient protection of the worker's body (protection of the head, hands, body, etc.)
- insufficient maintenance of equipment and machinery
- poorly designed business process or totally wrong process
- missing or weak data encryption
- lack of security cameras
- missing locks on office doors
- unrestricted upload of dangerous files
- URL Redirection to untrustworthy websites
- missing, insufficient or weak passwords
- missing Website SSL
How Aptien Can Help You Manage Vulnerabilities
- Knowing the vulnerabilities of your processes and assets will help you uncover potential risks
- See how you can keep track of vulnerabilities in Aptien Risk management