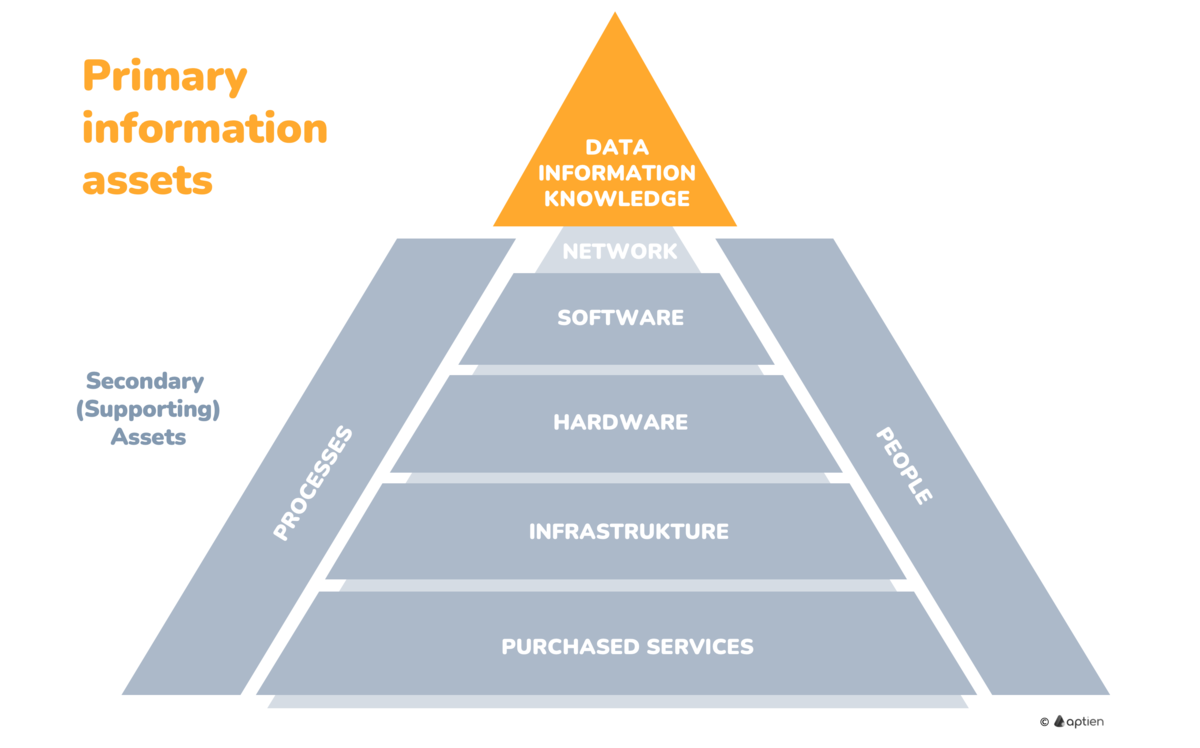
Information assets are the data, information, and knowledge that a business needs to operate and make decisions. These assets are stored, processed, or shared through software, on paper, or in people's minds. When primary assets are disrupted, the business cannot operate or make informed decisions, and management activities are affected.
- They are controlled and organized collections of data, information, or knowledge that hold value for the business.
- Primary assets depend on technology assets.
- Primary assets are only available if supporting assets are functioning and accessible.
See here how to identify information assets and examples.
What are the Most Common Information Assets in Companies?
Every business has its own set of information assets depending on its industry. However, most small and medium-sized businesses (SMBs) typically manage the following common types of information:
- Business data such as orders, project details, and sales information
- Customer Databases: Important client information including contact details and purchase history
- Financial Records: Balance sheets, income statements, and tax documents
- Employee Records: Personal information, performance reviews, and payroll details
- Research and Development Data: New ideas, test results, and product plans
- Company knowledge and expertise
- Product Information: Standard operating procedures, proprietary technologies (e.g., recipes, source code)
- Login credentials (for banking and other systems)
- All information classified as confidential
Information Assets Depend on Technologies and systems
Information assets need to be stored somewhere, whether that's in software, on paper, or even in people's knowledge. If these information assets are compromised, the business can't operate properly, and important decisions and management activities will be disrupted.
- they are connected to supporting technology assets that they rely on
- data is only accessible if these supporting assets are functioning correctly
How to keep information assets inventory
- How to keep a catalog of information assets see here
- For the purposes of complying information security standards such ISO 27 000 or NIS2, you must also keep the dependencies between information and supporting IT assets.
Why Small Businesses Need to Know Their Information Assets
- Identifying your information assets is the first step in evaluating security risks
- Along with potential threats and vulnerabilities, this helps you identify possible risks
- Learn how to find your key information assets here.