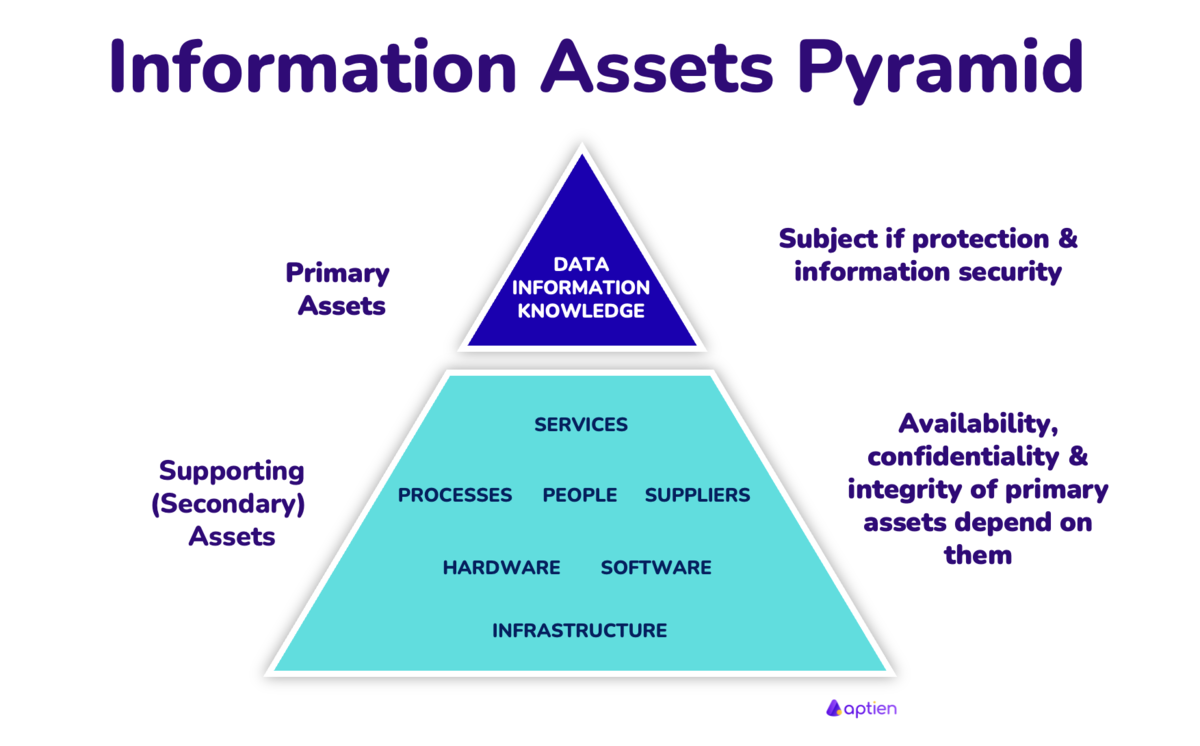
Definition of Information Security Pyramid
The Information Security Pyramid is a framework that helps identify dependencies and their relative importance during an information or cybersecurity asset analysis. It facilitates the prioritization and classification of information assets, which are the primary focus of information security efforts. Information assets are the fuel of business processes.
Importance of Information Assets:
Information assets are essential for decision-making, operations, and delivering value to customers. Here's why they are critical:
- Enabling Business Processes: Information assets—such as data, documents, and knowledge—are the inputs that drive core business processes. Without accurate and accessible information, processes can stall or fail.
- Strategic Value: Information assets often contain sensitive or business-critical data (e.g., customer information, financial records, intellectual property) that can directly impact competitive advantage and revenue
- Interdependency: Modern businesses rely heavily on IT systems to manage and protect information assets. A compromise in availability, confidentiality, or integrity can disrupt processes and harm business continuity.
Information Assets are the Subject of Protection:
- Because information assets are so integral, they become the primary focus of information and cybersecurity protection.
- Safeguarding them ensures business processes remain efficient, reliable, and resilient to threats.
- Data and information are the central subjects of information security and protection.
- These include data, information, and knowledge, which are the primary objects of protection in an information security strategy.
Dependency on IT assets:
- The availability, confidentiality, and integrity of information assets rely on supporting IT assets, which form the foundation of the pyramid.