Access Management is about controlling who can get into your business's physical locations (like the office), digital systems (like computers and software), and important files. It ensures that employees only have the access they need to do their job, and that this access is quickly removed when they leave or change roles.
What is Access Management for Small and Growing Businesses?
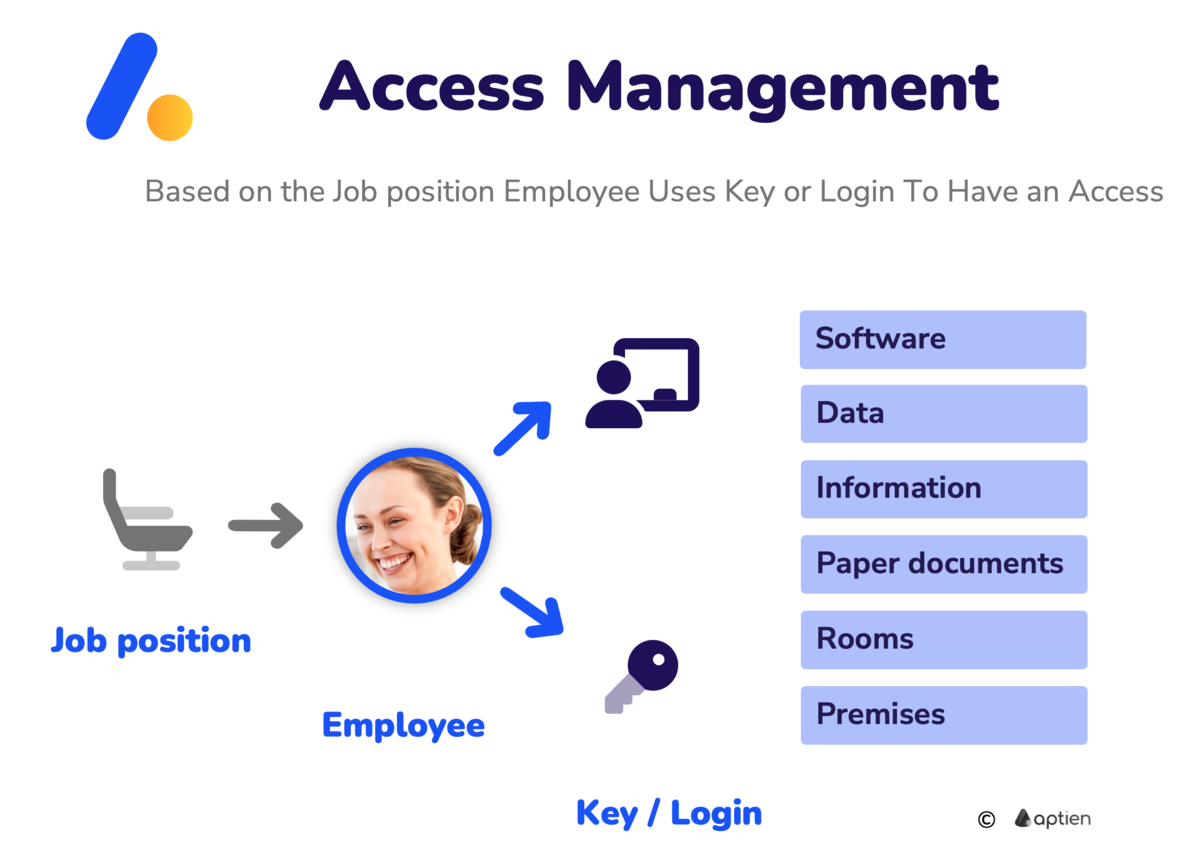
Access management means controlling who can access your company's physical spaces, digital systems, and important data. Essentially, it's about making sure the right people have the right access, and the wrong people don't. For any business, it's crucial for both physical and digital security.
Access management helps ensure that only authorized individuals have the necessary permissions to do their jobs, whether that's entering a specific building, logging into a system, or viewing sensitive customer information. Specifically, effective access management involves:
- Clearly identifying who is allowed access (e.g., employees, contractors, specific roles).
- Setting up, changing, and revoking access rights as people join, change roles, or leave.
- Using the right tools and technology to actually grant or deny that access.
What are the Ways to Control the Access
- technical means such as keys, cards, physical control, passwords, logins, and so on
- legal means, such as contracts, NDA, enforcement through policy or directive
What does it mean to have access control under control
1. You must correctly identify authorized persons
- Access control is based on accurate identification and authorization of individuals. This involves granting or revoking access rights based on job roles and responsibilities.
- Employees: Access should be granted to employees based on their specific job functions.
- External parties: Access to external individuals or third parties should be granted only after verifying their identity and signing appropriate contracts.
- This approach ensures that only authorized individuals have access to sensitive systems and data.
2. You must have technical means to grant or deny access
- Technical means provide some physical or digital barrier or protection
- This means keys, entry cards
- In the digital world, it is the use of some digital identity to verify users, such as a login
3. Support with legal means
- Legal means can supplement or replace technical means
- These include, for example, NDA, contracts, amendments, penalties
4. Correctly set processes for assigning, changing, and revoking permissions
- You assign permissions based on job
- You revoke permissions as soon as the work is done.
5. You must have everything correctly described in
- Access Control Policy
- Password Issuance Policy
- Key Issuance Policy
What does Unauthorized Access Mean
Unauthorized access means someone has gained entry to systems or information without permission, leading to a breach of confidentiality. This often happens due to poor management of access or external threats, such as:
- Giving access or permissions to the wrong person, or
- Not removing access when an employee changes roles or leaves the company
- Physical security incidents such as theft, break-ins, or other criminal act
Basic principles of Access Management
- Secure physical access to your office, computers, and network.
- Ensure only authorized individuals can access your company's systems and data.
- Manage what data and services employees can access within your business software.
- Restrict the copying of sensitive company data to personal devices or unauthorized storage.
- Control what types of email attachments can be sent or received to prevent malware and data breaches.
- Provide employees access only to the information and tools necessary for their specific job functions
What Key Business Processes are Crucial for Access Management?
Many organizations face challenges with access control, often because they lack robust processes for assigning, updating, or revoking user permissions. These issues are most evident during employee onboarding and offboarding.
- Granting initial access and permissions is a core part of employee onboarding.
- Revoking all access and permissions is a critical step in employee offboarding.
How Aptien supports an access management in the company
Aptien.com can potentially help with access management in several ways, depending on the specific features it offers. Granting and Revoking Access: Aptien could offer functionalities to grant or revoke access to specific systems, data, or functionalities within the platform based on user roles or individual permissions. Here are some possibilities:
Permission Management during Onboarding:
- Job Assignment: Upon hiring, during onboarding you could assign a pre-defined role based on the new employee's job position.
- Streamlined Access Provisioning: With role-based access control (RBAC), Aptien could simplify the onboarding process by assigning access to necessary resources based on the assigned job
- This eliminates the need for manual configuration and reduces the risk of errors.
- Onboarding Tasks and Training: Aptien might offer tools to manage onboarding tasks and training materials specific to different job roles.
- This ensures new hires receive the necessary training and permissions relevant to their position.
- Authorizations for External Parties: The platform might allow managing access for external parties, such as contractors or vendors, by defining specific permissions based on signed contracts.
Permission Management during Offboarding:
- Automatic Access Revocation: When an employee leaves, Aptien could automatically revoke access to all systems and data based on their previous job role. This ensures that former employees no longer have access to sensitive information.
- Offboarding Workflows: The platform might offer features to streamline the offboarding process by providing automated workflows for tasks such as collecting company property, updating user accounts, and finalizing payroll.
- Audit Trail: Aptien could maintain an audit trail of access changes, documenting who had access to what systems and when. This helps maintain compliance and accountability in case of security incidents.
Benefits of Using Aptien for Access Management
- Improved Efficiency: Automating access provisioning and revocation saves time and reduces administrative burden.
- Reduced Risk: RBAC ensures employees only access necessary resources, minimizing security risks.
- Enhanced Compliance: Aptien's audit trail helps demonstrate adherence to data security regulations.
- Streamlined Onboarding & Offboarding: Simplifies the employee lifecycle by automating key access management tasks.
How Aptien Helps with Access Management
Aptien enables you to effectively manage and record employee access to physical assets (e.g., keys, keycards) and digital resources (e.g., user accounts, software licenses) throughout their entire employment lifecycle, from hire to retire.
Centralized Employee Access View
- For each employee, get a comprehensive view of all assigned access.
- Assigned physical access (e.g., keycards, building keys)
- Assigned digital access (e.g., user accounts, software applications)
During Onboarding
- Streamline access planning for new hires, including keys, keycards, IT accounts, and software licenses.
- Ensure that all necessary access rights are assigned promptly and thoroughly documented.
- Easily assign user accounts and software licenses to employees.
During a Role Change
- Effortlessly update access based on new responsibilities (revoke old, grant new permissions).
- All changes are automatically documented within the employee's profile.
During Offboarding - Employee Departure
- Quickly identify what assets need to be returned and what access needs to be revoked (e.g., keycards, keys, accounts).
- Significantly reduce security risks during employee offboarding.
Comprehensive Access and Asset Tracking
- Aptien provides a centralized, comprehensive record of all physical and digital access assigned to individuals.
- Gain a rapid overview of who has access to what, essential for bolstering security, ensuring compliance, and simplifying audits.