Managing Access to Company Rooms and Other Physical Spaces
Managing access to company rooms and physical spaces means controlling who can enter buildings, different areas, individual rooms, and other designated spots. This helps make sure only authorized people can get in. Here are the main parts of access control for physical spaces:
Physical Company Infrastructure
- Access control relies on physical components like doors, gates, locks, and other barriers.
- These components physically block or allow entry based on permission.
- For example, a locked door prevents unauthorized people from entering a secure room.
Common Property Access Control Methods
Small and medium businesses use different methods to control who enters their spaces. The most common property access control systems include:
- Keys and physical locks: Traditional keys grant access to specific doors or areas. It’s important to manage key distribution and ensure only authorized employees have them.
- Keypad systems: Simple and cost-effective, these require entering a PIN code on a keypad to gain entry. They provide a basic level of security.
- Access Cards: Often RFID cards that allow secure entry. Each card is tied to specific access permissions.
- Access Tokens: Similar to cards, these electronic fobs grant access based on set rules.
- Biometric Methods: Using fingerprints, retina scans, or other biometric data for high-security access. These systems offer stronger security but can be more expensive to install.
- Other Authentication Methods: Some companies use PIN codes, smart devices, or mobile apps to control access.
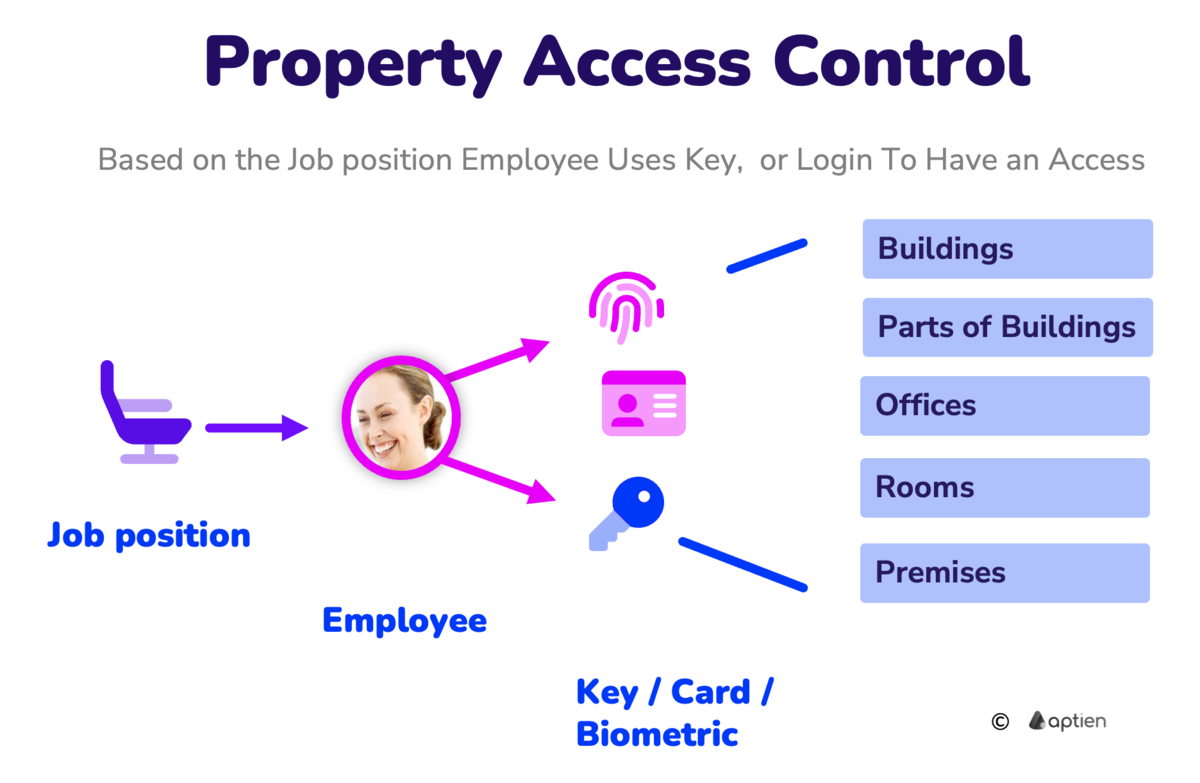
Job-Based Access
- Access rights depend on an employee’s role within the company.
- Job position determines which areas an employee can enter.
- For example, a manager might have access to secure conference rooms, while a janitor only accesses utility closets.
In summary, effective access control ensures the right people can enter specific areas while keeping your business secure. By managing keys, cards, tokens, and other authentication methods, companies can protect their physical assets and important spaces.
Managing Employee Access and Permissions with Aptien
Aptien offers an easy-to-use solution for managing employee access to your workplace, helping you keep things secure and running smoothly. Here are the main features:
Key Issuance During Employee Onboarding
- When new employees join your company, Aptien makes it simple to assign keys, access cards, or other permissions they need for their job.
- This streamlined process ensures employees can access the right areas in your facility from day one.
Access Control for Job Changes and Departures
- When employees change roles or leave the company, Aptien lets you quickly update or remove their access.
- If an employee’s job changes, you can easily adjust their access rights.
- When someone leaves, you can promptly deactivate their access cards or keys to keep your workplace secure.
Unified Overview of Employee Access
- Replace confusing spreadsheets with Aptien’s easy-to-use software.
- Get a clear view of who has access to which areas.
- Manage access smoothly to make sure permissions follow your security rules.
Notifications and Alerts
- Any changes to employee records, access, or permissions trigger alerts.
- Stay updated and keep your access management organized.
Audit Trail and History
- Aptien tracks all access and permission changes for each employee.
- This history helps ensure transparency and accountability.
Used Across Industries
- Teams from many industries trust Aptien.
- Whether you run a small office or a large facility, Aptien adjusts to fit your needs.
- With Aptien, you can ditch manual processes, reduce admin work, and boost security.