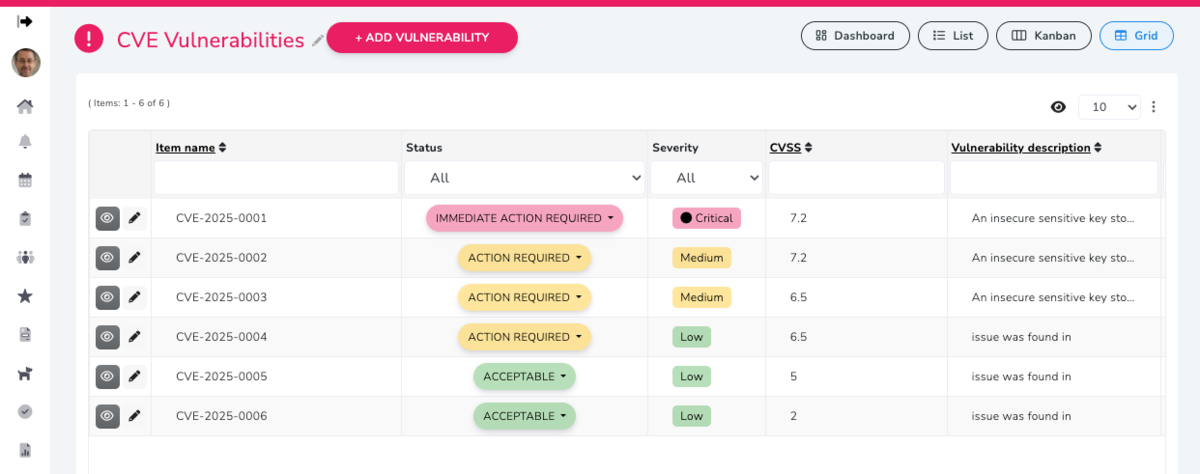
CVE (Common Vulnerabilities and Exposures) is a publicly available catalog of known security vulnerabilities, flaws in software and hardware. Each issue has a unique ID (e.g., CVE-2025-12345) so vendors, IT teams, and organizations can consistently reference, track, and fix it.
Why should SMBs care about CVE vulnerabilities?
CVE entries are tied to specific technologies—typically software, routers, servers, operating system versions, and similar business IT assets. A CVE is always linked to a specific product or version: a software application, operating system, or a hardware device that runs software/firmware. If you use a particular version, CVEs help you see whether it has known security weaknesses.
- With the CVE list, you can quickly check whether a vulnerability affects your environment. If a vendor announces that their product has “CVE-2025-12345,” you can assess its impact on your systems.
- Patches and updates: CVEs are linked to fixes and guidance. If you use software with a listed vulnerability, prioritize installing the patch or update as soon as possible.
How to remediate CVE vulnerabilities
- Patch management: the most important step is to regularly update systems, applications, and devices so known CVEs are addressed.
- If a fix is not yet available, apply compensating controls (e.g., configuration changes, network restrictions) or temporarily replace or isolate the affected technology.
How to automatically find which vulnerabilities affect your company
- With the CVE database, you can build a list of relevant vulnerabilities for your environment based on the products, IT assest and versions you use.
- Based on smart search, Aptien automatically alerts you to vulnerabilities that affect your company.